
As data breaches continue to proliferate, credential stuffing attacks have become rampant – and heavily automated.
A new report by Akamai today captures the scale: a mammoth 61 billion credential stuffing attempts in 18 months.
Credential stuffing is the automated injection of breached usernames/password pairs in order to gain access to accounts.
Attackers don’t even need pairs: a leaked email address and a lightweight brute force attempt to guess the password is often enough to pay dividends for an attacker, when “admin” or “password1” remain common.
With over eight billion email addresses leaked online alongside 555 million+ passwords – just the metrics captured by the “HaveIBeenPwned” database; the real figure is no doubt larger – every data breach is grist to the mill.
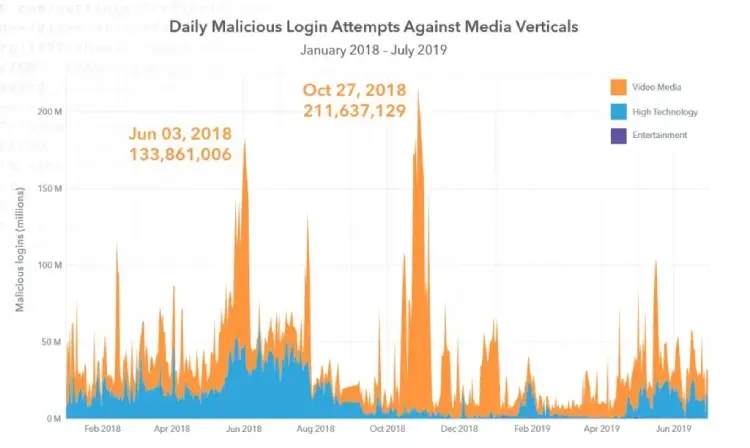
Akamai: Credential Stuffing
In a report focussed on the tech, video media and entertainment sectors, Cambridge, Massachusetts-based Content Delivery Network (CDN) and security firm Akamai notes that the three accounted for 35 percent of credential stuffing attacks over the January 2018 – June 2019 period it tracked.
“Our analysis indicates these three verticals are a stable and consistent attack source for two reasons: personal and corporate data. The targeted brands are household names, and criminals are looking to capitalize on that familiarity.”
By now almost completely automated, credential stuffing attacks are driven by All-in-One (AIO) applications like SNIPR or STORM, it notes.
“Some AIO programs are free, while others require an upfront registration fee. One of the more popular programs, SNIPR, will retail for about $20, while STORM is freely available online.”
Most AIOs also now come with pre-built evasion techniques for many default defensive measures, the company adds.
Read this: Magecart’s 7 Groups: Hackers Dropping Counter-Intelligence Code in JavaScript Skimmers
Looking more broadly at attack types against the three sectors, the security firm noted that SQL injections remained the top attack vector, accounting for more than 70 percent of attacks, followed by Local File Inclusion at 19.3 percent, Cross-Site Scripting at 3.9 percent, and PHP Injection at 3.3 percent.
Akamai adds; “Most criminals aren’t using sophisticated or specialized tools. They generally use the same legitimate programs widely available in numerous security offerings, including Metasploit and Kali Linux.
“Criminals with the skills to create bespoke tools are rarely noisy enough to show up in volume-based metrics, but they do exist.”






