
McAfee claimed today that 99 percent of IaaS misconfigurations initially go unnoticed by users. The claim is based on a combination of interviews with 1,000 businesses and anonymised customer data from “millions of cloud users and billions of events.”
“The enterprise companies we spoke to told us that they were aware of, on average, 37
misconfiguration incidents per month. Yet our real-world data shows that companies actually experience closer to 3,500 such incidents”, the security firm said.
It’s an eye-popping figure, somewhat leavened by data showing that 60 percent of incidents are fixed within an hour, but with the rapid rise of bots used to scan for insecure cloud buckets, that’s ample time for damage to be done.
McAfee, in the “IaaS Adoption and Risk Report“, blamed the velocity of cloud software deployments for the issue: “Much of this is automated by DevOps teams in the practice of CI/CD, which unfortunately automates misconfigurations along with all the rest… This means that misconfigurations are introduced, removed, or resolved on a constant basis as new infrastructure is rolled out.”
(The claim seems a curious one: while hyperscalers do, indeed, regularly ship code updates for their products, basic configuration and access settings rarely get changed as a result; while rapid code deployment frequently results in bugs, McAfee is not highlighting software vulnerabilities in its report, but actual configurations.)
Read this: Default Access for ‘Everyone’? New AWS Data Lake Service’s Settings Raise Red Flags for Security Experts
Unlike a typical desktop or server breach for which a phishing attack might be a typical initial vector, the risk of data exfiltration from the cloud often begins with this initial soft landing; rendered easy by such configuration issues.
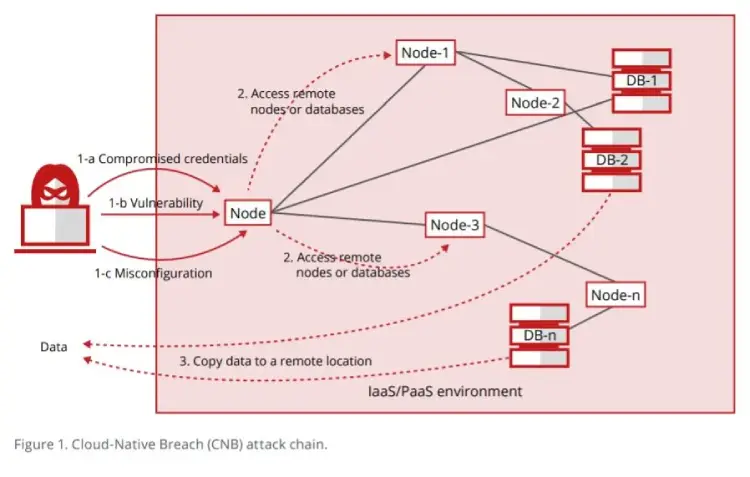
Cloud Native Breach and Privilege Escalation
Taking AWS as an example, McAfee said its data showed that “EBS data encryption” and “unrestricted outbound access” were the top two misconfigured settings, with EC2 security group port configuration in third place.
EBS, or Elastic Block Storage has a “public” mode that makes users’ virtual hard disk available to anyone on the internet. (Security firm Bishop Fox’s Ben Morris flagged that issue at security conference Defcon. AWS later said it had notified all customers who had that setting set to public. Again, the McAfee claim seems a striking one, although it is perfectly plausible, as with patching, that users simply aren’t paying attention to basic hygiene including of this known issue).
The misconfiguration of IaaS is central to attacks on cloud-based data: it can allow hacker access to part of a firm’s IaaS infrastructure they can build on by potentially escalating their privileges: McAfee found in its research that 58 percent of companies have experienced privileged user threats every month.
See also: 70 Applications, 15 Teams, 9 Months: Lessons from the Guardian’s “All-In” Move to AWS
The company gives a real-world example of the “Land-Expand-Exfiltrate” approach that ultimately resulted in the theft of over 100 million customer records. (McAfee appears to be referring to the Capital One attack. This did not start with a IaaS misconfiguration however…)
McAfee details that attack as follows:
1. “The adversary “landed” by exploiting a vulnerability using SSRF on a customer-deployed web application firewall (WAF)
2. “They then “expanded” by leveraging the exploit in the compromised node to query a metadata service to obtain sensitive keys and tokens. This allowed the adversary to obtain broad privileges, including the ability to query and read storage objects.
3. “Lastly, over 100 million customer records were “exfiltrated” from the storage object to anonymous nodes on the internet, and/or used tokens/keys from above step to invoke a custom script to copy storage object data to another storage object in another IaaS
account.”
McAfee’s research shows that cloud data loss from IaaS is rising and that incidents involving data loss via IaaS grew 248 percent year-on-year in 2018.






